I decided to try out atuin, a shell extension that writes your history to a SQLite database.
It's really neat. I wanted to see where the SQLite database lived on disk so I could poke around inside it with Datasette.
The documentation didn't mention the location of the database file, so I decided to figure that out myself.
I worked out a recipe using opensnoop, which comes pre-installed on macOS.
In one terminal window, run this:
sudo opensnoop 2>/dev/null | grep atuin
Then run the atuin history command in another terminal - and the files that it accesses will be dumped out by opensnoop:
501 51725 atuin 4 /dev/dtracehelper
501 51725 atuin -1 /etc/.mdns_debug
501 51725 atuin 4 /usr/local/Cellar/atuin/0.9.1/bin
501 51725 atuin -1 /usr/local/Cellar/atuin/0.9.1/bin/Info.plist
501 51725 atuin 4 /dev/autofs_nowait
501 51725 atuin 5 /Users/simon/.CFUserTextEncoding
501 51725 atuin 4 /dev/autofs_nowait
501 51725 atuin 5 /Users/simon/.CFUserTextEncoding
501 51725 atuin 10 .
501 51725 atuin 10 /Users/simon/.config/atuin/config.toml
501 51725 atuin 10 /Users/simon/.local/share/atuin/history.db
501 51725 atuin 11 /Users/simon/.local/share/atuin/history.db-wal
501 51725 atuin 12 /Users/simon/.local/share/atuin/history.db-shm
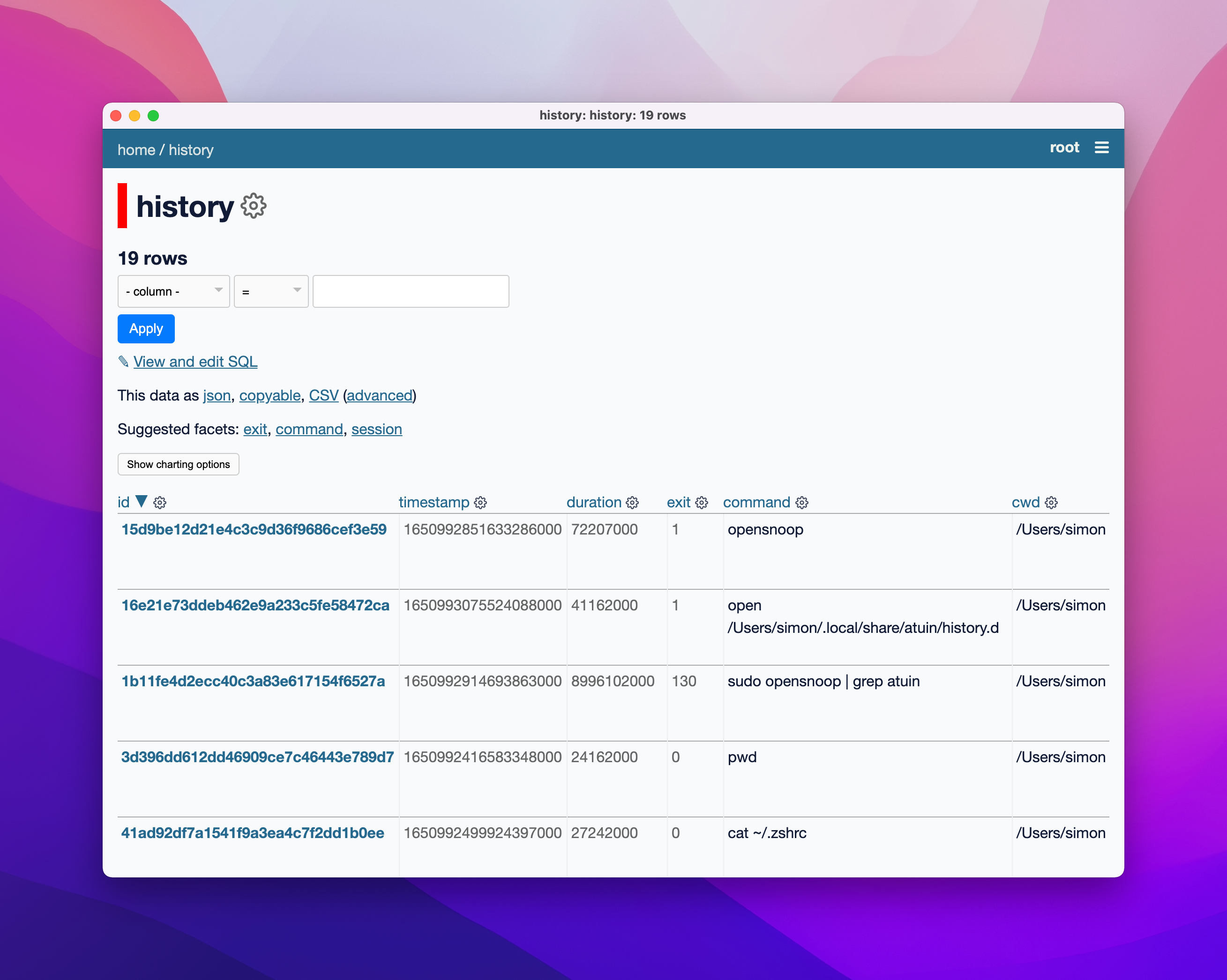
Then I ran open /Users/simon/.local/share/atuin/history.db (because I have Datasette Desktop installed) and could start exploring that database:
The 2>/dev/null bit redirects standard error for opensnoop to /dev/null - without this it spews out a noisy volume of dtrace: error ... warnings.
My Twitter thread asking about this resulted in a bunch of leads that I've not fully investigated yet, including:
- FileMonitor
- FSMonitor
iosnoopfs_usagesudo dtrace -n 'syscall::open*:entry { printf("%s %s",execname,copyinstr(arg0)); }'strace(Linux, not macOS)